MSSP Software: The Proactive Features
As compliance requirements become standard expectations for companies of all sizes, many organizations are turning to managed service providers (MSPs) and managed security service providers (MSSPs) to strengthen their defense posture.
The toolset required for service providers to rise to the challenge of increasingly prevalent cybersecurity threats can be divided into reactive and proactive tooling.
Reactive tools are essential for routine security management activities, including incident detection and recovery, and system patching. Reactive measures address active risk and threats. In contrast, proactive measures build stronger defenses by identifying and resolving vulnerabilities before they can be exploited, reducing the attack surface, probability, and severity of a security incident. Proactive tools help service providers inventory assets within their client environments, uncover and prioritize vulnerabilities, and achieve regulatory compliance. They also enrich reactive tools with information to make them more effective.
More importantly, proactive software capabilities enable providers to offer new services that are viewed as strategic by their clients’ executive management, command a higher profit margin, and help develop strategic partnerships with clients.
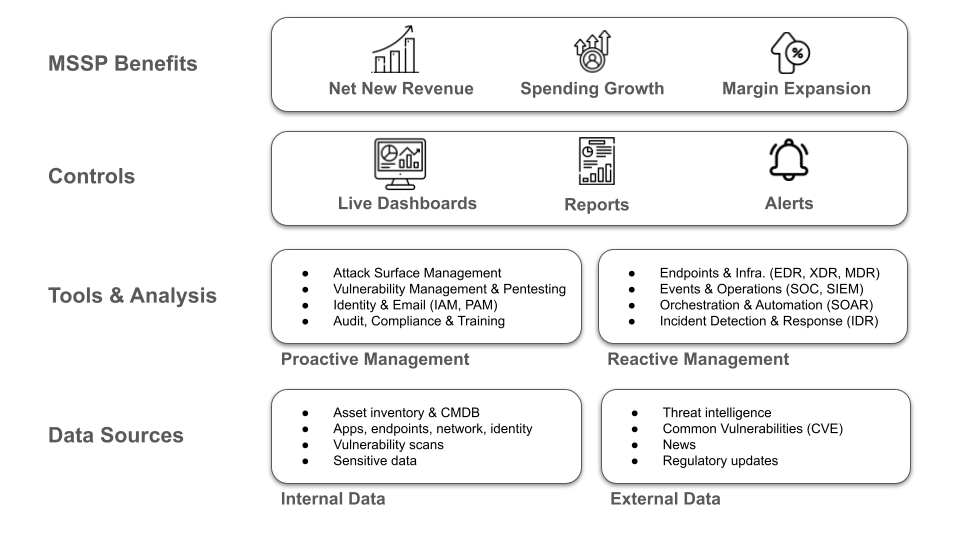
This article focuses on the essential features that comprise the proactive management category of security software functionality. Whether you’re an established MSSP refining your service model or a new provider looking to expand into security, this article should help you with ideas and best practices to generate new high-margin revenue for your practice.
{{banner-large-1="/inline-cards"}}
Summary of essential MSSP software features for proactive management
Asset discovery and endpoint security
Risk scales with the number of client environments under management. For MSSPs, asset discovery and endpoint protection provide the baseline for managing multi-tenant environments. Centralized visibility facilitates the earlier detection of anomalous behavior and ensures that endpoint protections are consistently enforced across client environments.
MSSPs benefit when discovery and endpoint protection run through a single platform. This is because they can onboard clients faster, easily maintain compliance reports, and demonstrate measurable coverage during service reviews.
Consolidation also reduces tool sprawl, allowing analysts to focus on higher-value analysis, such as correlating asset classes with incident frequency or identifying risk introduced by configuration drift. This kind of closed-loop, automated visibility is what distinguishes leading MSSPs from those relying on fragmented toolchains.
Features to look for
Modern MSSP platforms implement automated asset discovery to continuously enumerate devices, systems, and applications across client networks. Automated discovery operates on a rolling cadence and captures changes as configurations shift. This approach reduces blind spots, exposes unmanaged or rogue assets, and establishes a reliable baseline for downstream security monitoring and response.

Once assets are identified, integrated endpoint security provides the next layer of control. Endpoint telemetry is streamed into a centralized management plane, allowing analysts to assess system health, verify security configurations, and respond when controls drift from defined baselines.
Ultimately, asset discovery and endpoint security underpin all downstream MSSP functions. They provide analysts with the necessary context to make informed decisions and maintain steady, reliable operations. Without this foundation, security programs become haphazard and spotty.
Threat intelligence
Threat intelligence enables service providers to learn from multiple enterprise environments across the industry and provide context for vulnerabilities and incidents that occur in their own client environments. Strong intelligence capabilities enable security analysts to anticipate attacks rather than react to them in isolation.
Correlation engines extend intel-driven analysis by adding context directly to alerts. Analysts can more reliably separate background noise from indicators that warrant investigation or response. Analyst triage time reduces as the software consolidates context that would otherwise require manual lookup across multiple tools.
Features to look for
Modern MSSP platforms integrate intelligence from a variety of sources, including open-source exchanges and commercial feeds such as MISP. These feeds are continuously correlated with internal telemetry to improve detection fidelity and reduce false positives.
Instead of listing individual indicators, the system correlates information to uncover attack campaigns, recognize known malicious behaviors, or analyze historical patterns tied to that indicator. Properly implemented correlation improves alert quality. However, overly aggressive suppression logic introduces coverage gaps if benign-looking activity masks early-stage or low-signal threats.

Example: Cross-client threat detection through correlation
A SIEM generates an alert for one client related to unusual outbound traffic. In isolation, the signal is ambiguous. However, once the alert is enriched with intelligence, the platform reveals that:
- The destination IP has recently been tied to a C2 server used in a new malware campaign
- Several other clients have attempted connections to related infrastructure
- The pattern matches a cluster of activity seen spreading across similar industries.
With all this information in mind, the MSSP analyst escalates the incident, deploys proactive controls across multiple tenants, and initiates targeted containment steps. Instead of managing isolated investigations, the provider can respond to a coordinated threat with a coordinated defense.
Data security
MSSP software must be capable of securing data at every stage of its lifecycle while aligning with the governance and privacy requirements that vary across industries and regulatory frameworks.
Integrating DLP (Data Loss Prevention) and SASE (Secure Access Service Edge) allows MSSPs to apply consistent policies across endpoints and applications. DLP detects, monitors, and blocks the unauthorized transfer of sensitive data across an environment. CASB specifically acts as a security enforcement point between users and cloud services, applying these DLP policies and enforcing security controls for cloud applications. These controls monitor access and data movement patterns, generating actionable signals when activity deviates from approved usage or governance rules.
When these controls operate together, they enable MSSPs to meet governance and privacy expectations without introducing unnecessary complexity. This unification also improves day-to-day operations. A single dashboard might highlight sensitive data stored in an unapproved location, prompting the MSSP to apply corrective safeguards. Since classification, protection, and policy enforcement all flow through one view, the response is fast and straightforward.
Features to look for
Modern MSSP software should provide layered data security controls. Encryption protects information both in transit and at rest. Tokenization adds another layer to this by replacing sensitive values with non-exploitable substitutes. For example, it replaces sensitive data, such as credit card numbers or account details, with a non-sensitive, randomly generated value, so the data would not be valuable to attackers if breached.
Data classification features extend this protection by identifying which assets actually contain sensitive information. Automated classification scans both structured and unstructured content to assign sensitivity labels, such as PII, PHI, or PCI. However, these classifications are not authoritative in isolation. Information, such as business context, operational requirements, and risk tolerance, often requires additional manual validation and approval, typically through CISO-led risk analysis or governance workflows. Once properly categorized, these datasets can be governed with the appropriate policies.
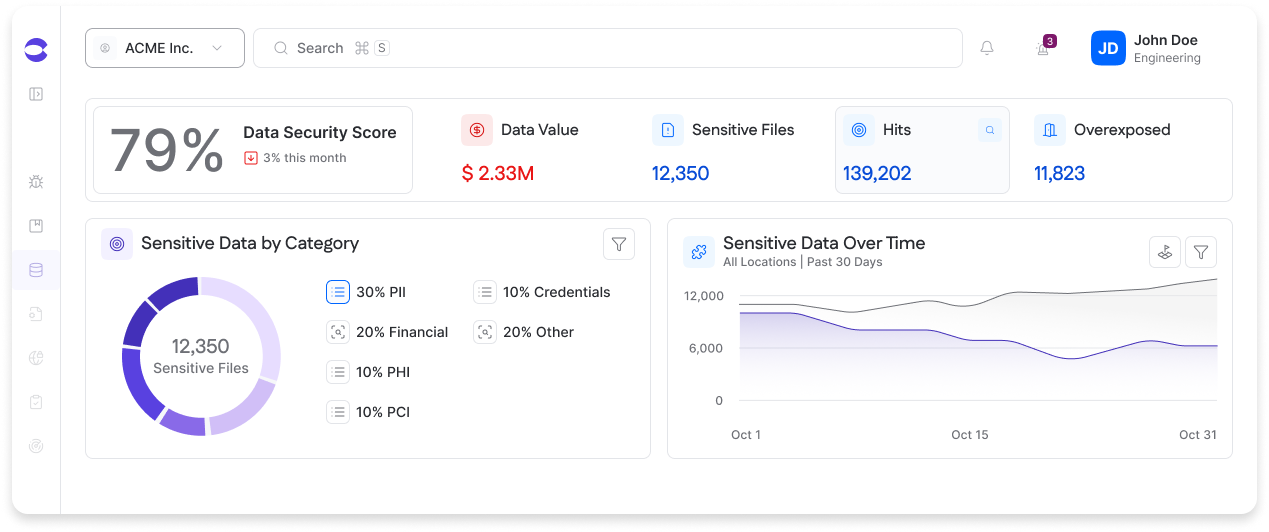
Strong data security is more than just a compliance obligation. It’s a core trust signal. Clients want assurance that their information is handled responsibly and securely. MSSPs that provide visibility make trust easier to earn and develop strategic partnerships with their clients.
{{banner-small-1="/inline-cards"}}
Vulnerability scanning and patching
Proactive vulnerability management reflects the maturity of MSSP operation workflows. It supports a more accurate and current risk posture across managed environments.
Features to look for
MSSP software should include continuous scanning to identify high-risk weaknesses and configuration issues as they emerge. This gives analysts the insight needed to reduce exposure before threats can materialize.
It should support automated patching to link vulnerability identification directly to remediation workflows. This way, analysts can assess, prioritize, and remediate known Common Vulnerabilities and Exposures (CVEs) within a single operational pipeline.
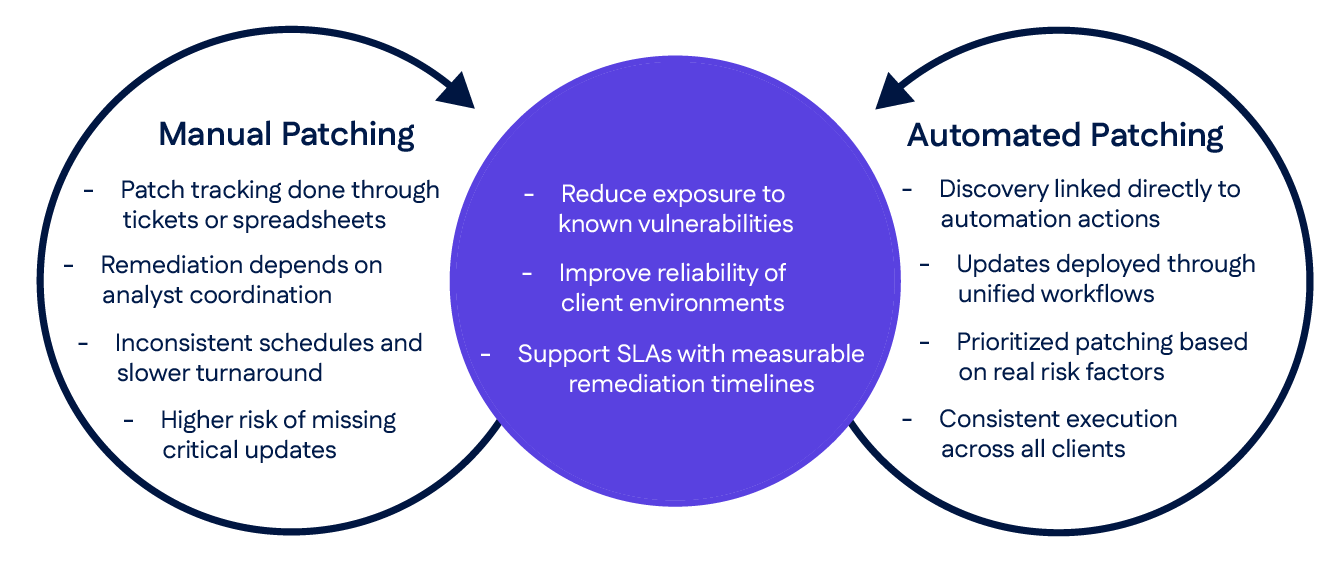
The software should also provide a patching dashboard to track remediation timelines for critical CVEs across client environments where delayed patch cycles threaten Service Level Agreement (SLA) commitments. By directly linking vulnerability findings to remediation status and service performance indicators, MSSPs can assess effectiveness, identify bottlenecks, and align remediation efforts with agreed client requirements.
Identity and access management
Managing access across multiple clients with heterogeneous environments requires centralized control over roles and privileges. MSSPs are expected to enforce least-privilege access. Integrations across cloud and on-prem systems should simplify credential management and make it easier to apply consistent rules across every client environment.
Features to look for
MSSP software should enforce IAM principles through a single console, making compromised accounts far less likely to escalate into major incidents. A practical example is the deployment of multi-tenant IAM policies through a single central interface.
Rather than configuring access separately for each client environment, MSSPs can use the console to define and apply standardized controls across accounts, roles, and applications. This creates predictable and repeatable workflows, which are critical for both security and scalability.
Well-defined IAM controls also support downstream security functions. When identity controls are straightforward and consistently enforced, analysts spend less time troubleshooting access issues and can focus more on higher-value security functions.
Here are some widely recognized frameworks that outline IAM best practices and help MSSPs align their access control policies with industry standards.
Compliance checking
Automating control tasks used to verify compliance enables providers to scale their services, reduce labor costs, enhance profit margins, and maintain the level of transparency clients expect. When assessments run continuously, the compliance status reflects the current state of the environment rather than a static snapshot.
Features to look for
Modern MSSP software has features to monitor client environments against established frameworks such as NIST, ISO, HIPAA, and CIS. Automated controls evaluate configurations and security posture against framework requirements, surfacing deviations as they occur. This continuous assessment helps prevent configuration drift and keeps environments aligned with regulatory standards throughout their lifecycle.
Centralized compliance dashboards make these assessments operationally actionable. MSSPs can rely on a unified view backed by runtime checks and API-driven validation rather than gathering evidence from fragmented sources (e.g., spreadsheets, ticketing systems, documentation repos, etc.)
Configurable report templates further streamline compliance workflows by generating reports aligned with client-specific regulatory requirements. This transforms compliance from a manual, reactive service into a measurable, well-structured operational function.
Platforms like Cyrisma offer compliance scoring dashboards with live status indicators for each standard. This gives MSSPs and their clients an instant view of progress and outstanding requirements. This visibility is particularly important when managing multiple regulatory frameworks across diverse client industries.
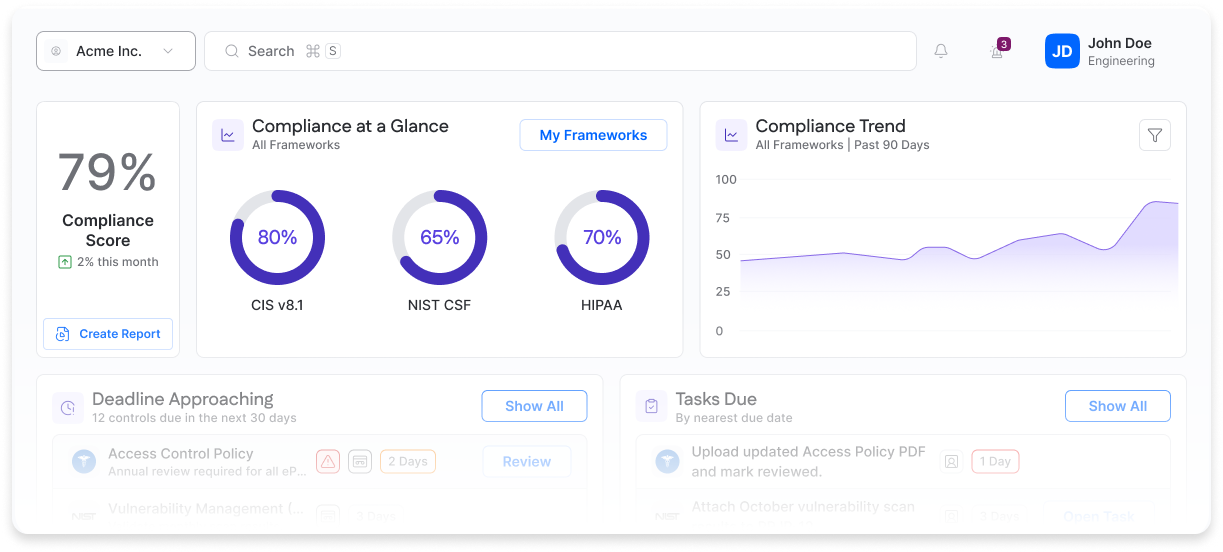
The following table shows how capabilities commonly found in platforms like Cyrisma map to key stages of the compliance process:
Penetration testing
Penetration testing provides a validation layer that complements vulnerability scanning, offering a more comprehensive approach to security. While vulnerability scans identify weaknesses, pentesting shows how these weaknesses behave under real attack conditions. Regular validation enables MSSPs to verify whether implemented controls effectively limit attacker movement and whether remediation efforts result in measurable risk reduction.
Features to look for
Modern MSSP platforms should support automated pentesting capabilities that simulate common attack paths at scale. These exercises test resilience, expose privilege escalation routes, and reveal opportunities for lateral movement. Since the simulations are repeatable, MSSPs can assess environments consistently across clients and track improvements over time.
Example: Linking pentest findings with vulnerability data
Scenario: A routine pentest identifies that an internal application allows unauthorized directory traversal. In isolation, the finding indicates a misconfiguration. When combined with recent scan data, additional context emerges.
- The system also contains an unpatched CVE related to input sanitization
- The affected server hosts sensitive client records
By correlating these efforts, the MSSP can demonstrate not only that the vulnerability exists but also how it can be exploited in practice and the business impacts it could have. After remediation, a follow-up test confirms that the attack path is closed, providing concrete evidence that risk exposure has been reduced.
Continuous validation strengthens trust by showing outcomes. By presenting before-and-after results tied to specific attack paths, MSSPs can objectively demonstrate changes in exposure rather than relying on assumed control effectiveness.
MSSP software checklist
As MSSPs grow, challenges such as tool sprawl, alert fatigue, and rising operational costs can erode both efficiency and profitability. Delaying the decision to upgrade the tooling required for proactive security management and higher profit margins can threaten the competitiveness of MSSPs in the market.
The following five capabilities represent the most important features to consider when assessing MSSP-ready software:
Unified platform
A single, cohesive interface reduces context switching and shortens investigation time. When everything you need to know appears in one place, analysts spend their time actually resolving issues rather than navigating tools.
Multi-tenancy and non-linear scaling
Service provider-grade multi-tenancy enables MSSPs to manage multiple clients from a single environment without duplicating infrastructure or workflows. Platforms that can scale without proportionally increasing cost or analyst workload support long-term growth.
Risk quantification
Translating technical findings into financial impact gives MSSPs a strong argument for communicating risk and justifying remediation priorities. Quantification also helps clients understand the business implications of delayed patching or config drift.
Automated remediation and one-click actions
Efficiency increases when routine fixes can be executed directly from the platform with a single mouse click. This workflow automation enables MSSPs to react in seconds, maintain SLAs, and minimize manual overhead.
Templated reporting
Pre-built report templates integrated with tooling platforms provide a foundation for reporting on risk assessment or regulatory compliance, while still allowing for customization for each client as needed. This ensures consistency and saves time when onboarding new clients.
{{b-table="/inline-cards"}}
Final thoughts
MSSPs must upgrade their tooling platforms to accelerate onboarding of new clients, reduce expenses, and offer services relevant to the market. Key principles to keep in mind:
- Visibility is the foundation. Asset discovery and endpoint security create the context needed for every other security function to operate effectively.
- Intelligence improves decision-making. Threat intelligence enables MSSPs to understand which events are most critical and respond with greater confidence.
- Protecting data is non-negotiable. Strong data security practices ensure that sensitive information remains secure across all environments.
- Proactive controls reduce exposure. Continuous scanning and automated patching shorten remediation time, which strengthens client trust.
- A unified platform accelerates growth. Multi-tenancy, automation, and integrated reporting reduce overhead and support profitable MSSP operations.
Whether optimizing an existing service model or expanding into managed security for the very first time, aligning MSSP software with modern security principles ensures both resilience and long-term growth.



