Vulnerability Prioritization Best Practices
In the modern cybersecurity landscape, businesses face more challenges than ever before, including higher threat counts, increased complexity, and rapidly changing regulations, among others. This increased pressure is magnified for security service providers, who have to work harder than ever to keep up. These service providers may be managed service providers (MSPs) or managed security service providers (MSSPs), serving multiple clients, or centralized IT organizations within large enterprises that serve various lines of business. Either way, they face a large number of vulnerabilities across vast, disparate environments and must ask themselves: “Where to start?” The idea of prioritization isn’t optional for them; it's fundamental to reducing client risk in an impactful way while balancing limited time and resources.
The right approach to vulnerability management varies by each organization’s unique situation. When more than 52% of all vulnerabilities are scored “High” or “Critical”, prioritization beyond technical scores is paramount. This contextual data includes business impact, severity, criticality, governance, and more, ensuring that an accurate rating is used to prioritize efforts based on the organization's unique needs.
Security service providers must transition from traditional technical scoring to risk-based scoring in order to economically manage multiple clients with unique environments, business-critical assets, and regulatory obligations. This transition will enable security service providers to align their clients' investments with their risk posture, ensuring that internal resources are spent efficiently while increasing their scalability and profitability. This article explores key best practices for vulnerability prioritization from the perspective of managed security service providers.
Summary of key vulnerability prioritization best practices
The table below summarizes the essential best practices covered in this article.
{{banner-large-1="/inline-cards"}}
Risk management lifecycle
The risk management lifecycle for vulnerability prioritization is represented below. This is a continuous process to enable organizations to manage security weaknesses in their IT assets proactively. It involves the following stages:
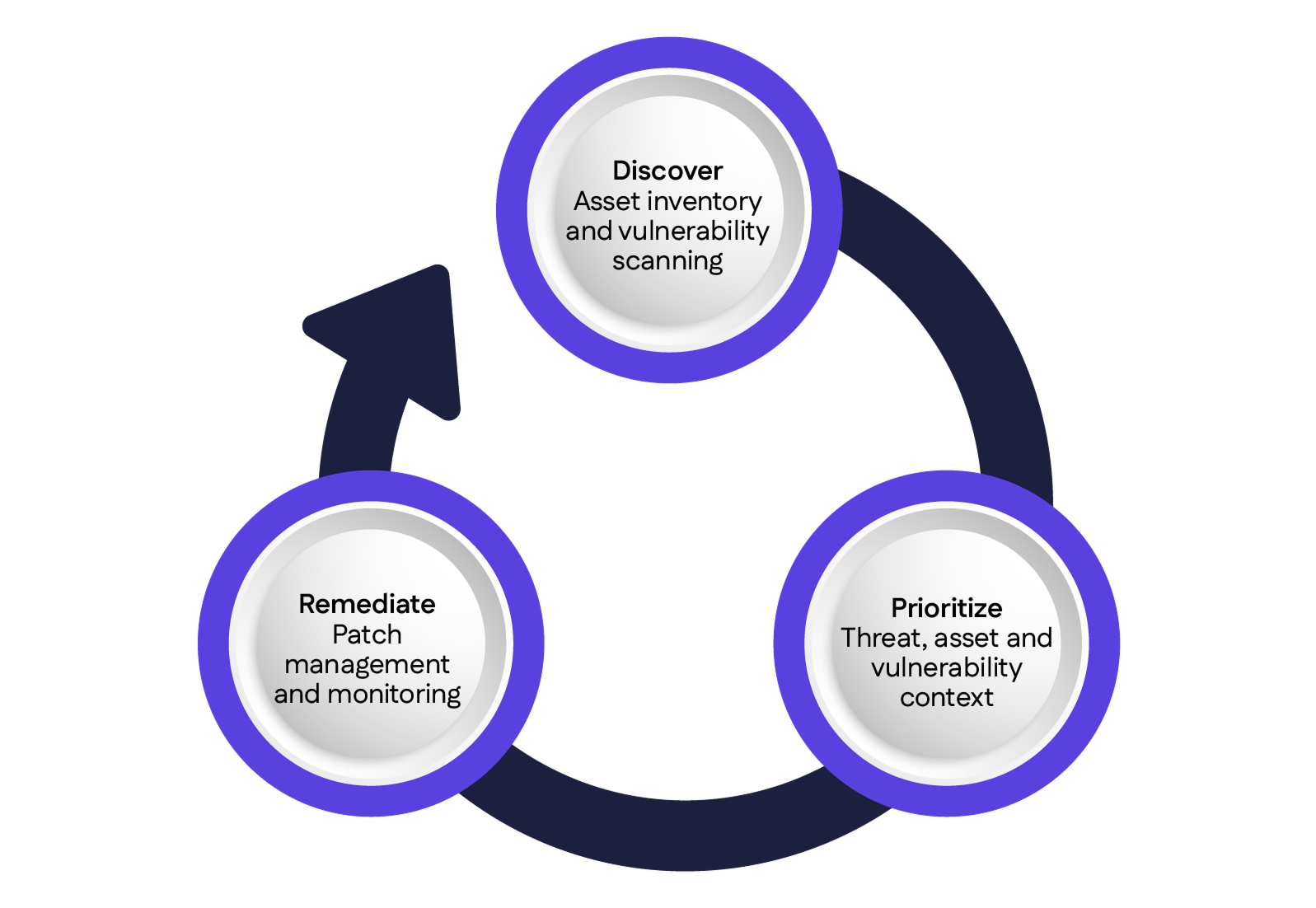
Risk management lifecycle for vulnerability prioritization (source)
Many organizations continue to prioritize vulnerabilities based solely on technical scores (such as CVSS), but these scores only tell part of the story. Exclusively using technical scores for prioritization results in predictable inefficiencies, such as allocating resources to patch low-impact systems (e.g., development servers) while lower-scoring vulnerabilities remain on business-critical production systems. Additionally, it consumes scarce and expensive resources on remediating vulnerabilities that may not materially improve the organization’s resiliency.
Prioritization is a fundamental, proactive step in managing risk. Without proper guidelines in place for this step, organizations will struggle to manage risks effectively, both from a risk and cost perspective.
Adopt a risk-based approach
Traditional vulnerability prioritization relies on technical scores such as CVSS. While these technical scores are essential, they do not reflect:
- Asset criticality
- Business impact
- Likelihood of exploitation
- Active exploitation in the wild
- Cost of remediation vs. cost of exposure
- Root-cause vs. symptom analysis
- Unique client priorities (e.g., governance and regulation)
Logically, patching a medium-severity vulnerability on a public-facing VPN concentrator is a higher priority than patching a high-severity vulnerability in a lab environment. Technical scores do not capture these risk dimensions, so adopting a risk-based approach is critical for service providers. Additionally, we should determine whether the vulnerability is a root cause or a symptom of a broader issue. If it’s the latter, then priorities may shift. For example, evaluating whether patching an aging piece of equipment is the right approach or whether retaining that asset is for a specific reason. Asking these questions ensures that we’re addressing the actual issues rather than treating symptoms and unintentionally leaving deeper issues in place.
Risk-based systems focus on the following:
These risk dimensions are used to create a hybrid score that combines technical risk, business impact, and exploitability to more accurately describe the risk posed to the organization by a vulnerability:
Hybrid Score = (CVSS Severity × Business Impact Weight) + Exploitability Modifier
Throughout this article, we will use the above formula to demonstrate how additional data on assets or vulnerabilities can provide insight and alter priorities. Note that these calculations are almost always automated, but illustrating these calculations is informative. Using this formula, we can revisit the above example. A public-facing VPN with a medium severity could be defined as having the values CVSS Severity = 7.8, Business Impact = 1.5, and Exploitability Modifier = 2. This results in a Hybrid Score of (7.8 x 1.5) + 2 = 13.7. Looking at the numbers for the lab system, we see something like: CVSS Severity = 9, Business Impact = 0.4, and Exploitability Modifier = 0. This gives a score of (9 x .4) + 0 = 3.6, which more accurately reflects the risk. Note that the weights above are arbitrary, but they must be consistent across all vulnerabilities.
Integrating threat intelligence
Without accurate information regarding threats, exploitability is often guesswork. Exploitability has two components. One we spoke of earlier is how easy it is for a system to be accessed by threats: If a system is public-facing, this component will be higher. The second component is the frequency with which the vulnerability is observed in the wild; it is primarily gathered using threat feeds. Exploitability is equally fundamental to severity and helps organizations concentrate resources on vulnerabilities with a higher likelihood of exploitation.
The following questions are answered to score exploitability:
- Is the vulnerability actively being exploited?
- Are there publicly available exploit tools/code?
- Is the vulnerability being targeted by groups?
Threat-aware prioritization allows service providers to avoid firefighting and remain proactive. It also helps them justify action and communicate urgency to clients. Threat intelligence feeds can originate from a broad range of sources, including open source communities, security firms, or national agencies. Some popular examples include CISA’s Automated Indicator Sharing program, Spamhaus, and Cisco Talos. No single threat feed is enough to provide a clear picture of threat actor activities at large, though; typically, organizations combine multiple feeds to create a composite that provides additional clarity.
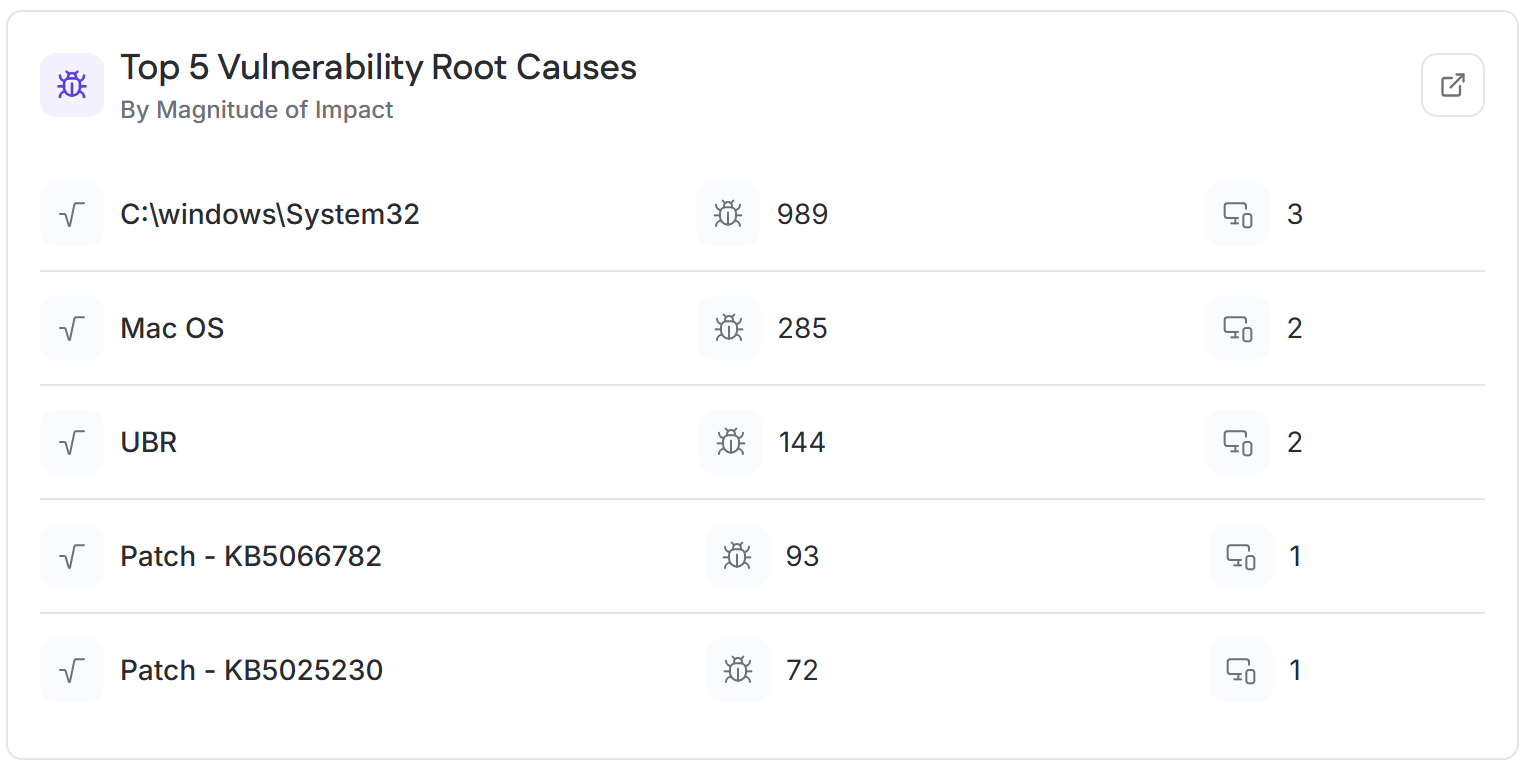
Organizations can calculate a composite exploitability score by averaging how frequently a threat is observed across multiple feeds, then add that number to a context-aware exploitability index to create an accurate description of how likely exploitation of a vulnerability is, incorporating all variables. To demonstrate this, let’s imagine that our VPN vulnerability from earlier has been seen in the wild frequently but not often enough to be ubiquitous, giving it a score of 3. This would result in our equation being:
CVSS = 7.8, Business Impact = 1.5, Exploitability = 2 + 3
Hybrid Score = (7.8 x 1.5) + 5 = 16.7
To reiterate, these numbers are arbitrary but must be consistent across all scoring.
Align vulnerabilities and assets
For service providers to prioritize effectively, they must maintain a matrix of assets and vulnerabilities. The following represents a fundamental matrix:
- Asset
- CVEs present
- Severity
- Exploitability
- Business value
- Exposure level
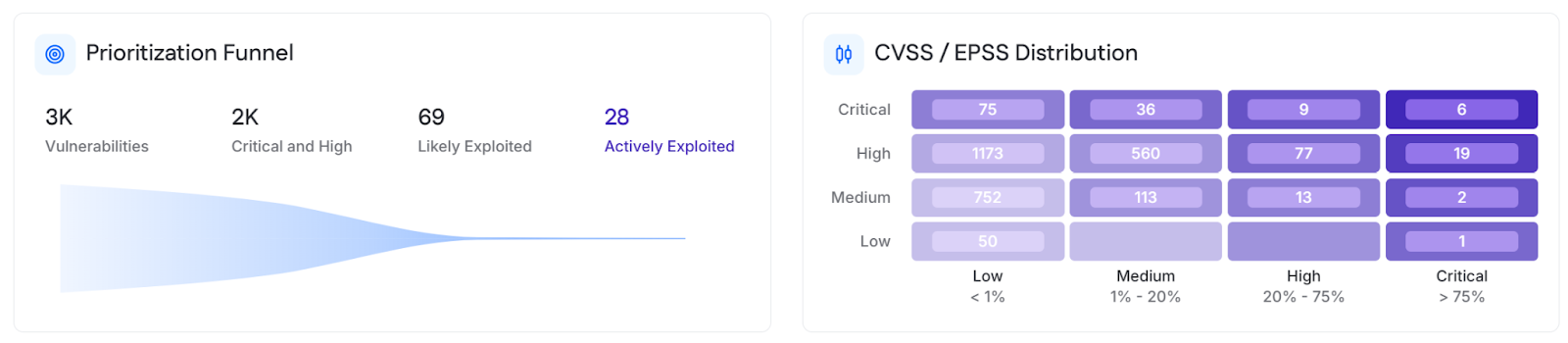
Maintaining a matrix of the listed qualities enables organizations to prioritize based on the displayed factors without requiring additional labor. This matrix can also be used to support functions such as visualizing risk, supporting governance initiatives, and communicating security value to clients.
{{banner-small-1="/inline-cards"}}
Automating the workflow
Automation allows service providers to scale, remain profitable, and provide consistent, repeatable results to clients. These benefits, along with the inherent complexity of vulnerability prioritization, make automation an obvious choice. Some everyday tasks to automate include:
- Grading vulnerabilities based on standardized logic and asset tagging
- Automated task creation and ticketing
- Auto-remediation where appropriate (patch installs, simple config fixes)
- SLA-based escalation workflows
- Gathering of vulnerability data
Most enterprise organizations rely on a combination of SIEM and SOAR products to automate security tasks.
Grading vulnerabilities can be automated using asset tags. These tags can provide context for assets; for example, a tag could indicate whether an asset is public-facing or a lab or development asset. Asset tags can be used to notate most types of context, including asset criticality, data classification, network exposure, and compliance. These tags can be multi-valued expressions to lend more context, such as public-facing, internal-only, or DMZ for network exposure. These tags must then be mapped to values associated with the hybrid scoring equation. For example, the asset tag network “exposure = public-facing” would map to an exploitability of 2 in our example. Maintaining a proper set of asset tags is critical to risk-aware automated scoring; without the context they provide, automated scoring systems will lack the knowledge necessary to assess risk.
After a vulnerability has been scored, appropriate action can be taken. The vulnerability should be resolved autonomously wherever possible. If the vulnerability can’t be remediated automatically, a ticket should be automatically created. Service providers are familiar with ticketing automation as a vital part of day-to-day life. When making a ticket for a vulnerability, the vulnerability information must be included in the ticket. At a minimum, the following data should be included:
- Hybrid risk score
- Asset name and asset tags
- Vulnerability description
- CVE link
- SLA
This automated ticket serves several purposes: establishing a record of activity, helping security service providers track and manage effort, and allowing security tasks to be tied to an SLA. These purposes are all vital to efficiency and customer satisfaction, which is why every successful service provider uses automated tickets for numerous tasks.
Link prioritization to governance and reporting
Although prioritization is not a formal part of governance, risk, and compliance, priorities should be informed by the organization’s chosen framework. The most efficient way to perform this mapping is to use a tool such as Cyrisma to correlate vulnerabilities with frameworks and standards.
Mapping these vulnerabilities manually is a massive effort and is not economical for MSPs and MSSPs because they must manage multiple clients with their own compliance and governance needs. Aligning vulnerabilities to recognized standards such as NIST CSF 2.0, ISO 27001, or PCI DSS ensures that a client's security investment aligns with their security posture. These mappings also help service providers communicate their clients’ security posture using predefined, widely understood standards, further reducing duplication of effort.
For example, mapping the actual remediation work, such as patching, applying configuration baselines, removing legacy services, or tightening access controls, to the NIST CSF 2.0 Identify and Protect functions shows how targeted remediations can reduce risk across asset management, access control, and vulnerability management domains. This provides a defensible way to demonstrate the impact of remediation efforts and simplifies reporting to stakeholders via established governance frameworks.
Automation tools are designed to streamline this mapping process by eliminating manual cross-referencing and reducing operational overhead. As a result, service providers can use consistent messaging to communicate the value of security activities and advise clients on prioritizing the vulnerabilities that pose the highest risk to their selected posture. This consistent communication is built into standards and frameworks; however, using automation tools to map these standards ensures consistency throughout the process, leading to more efficient communication and higher client satisfaction.
Frequently reassess
The threat landscape is constantly changing, just as client environments are. Service providers must frequently reassess their clients’ environments to ensure that vulnerabilities and priorities reflect the current state of both the environment and the broader threat landscape. Here are some methods that allow for more frequent visibility and reassessments:
- Continuous vulnerability scanning
- Scheduled vulnerability scanning (monthly/quarterly)
- Quarterly automation reviews
- Weekly exploit feed updates
- After-action reports: lessons learned
Risk scoring and remediation must continue to evolve ahead of risk to remain proactive. Information must be frequently updated; that also applies to service providers’ policies and procedures. If either of these elements falls behind the risk landscape, organizations lose the opportunity to be truly proactive.
MSSP software requirements for vulnerability prioritization
Selecting software for vulnerability prioritization is fundamental to modern cybersecurity efforts. Here is a table of features that service providers should prioritize when searching for a vulnerability management solution.
{{b-table="/inline-cards"}}
Last thoughts
Cybersecurity budgets, decision-maker attention, and labor are finite resources. As vulnerability numbers, regulatory requirements, and complexity continue to balloon, MSPs and MSSPs must focus their efforts on the issues that matter most. With proper prioritization, MSPs and MSSPs can ensure that limited resources are allocated where they have the most significant impact, leading to more consistent service for clients, healthier margins, and reduced operational strain on their technical teams. Taking a risk-based approach and automating prioritization workflows are giant first steps that will have a resounding impact on both service providers’ internal teams and their clients’ risk posture. Cyrisma can help make these first steps efficient and straightforward while providing additional tools, such as mapping vulnerabilities to frameworks and regulations.
Regardless of the tools, the process for prioritizing vulnerabilities remains focused on creating the information that drives decisions and processes to align security investments with risk postures in the most efficient manner possible.



